Agari releases findings of new quarterly email security trends report
Agari, the next-generation Secure Email Cloud that restores trust to the inbox, released the findings of its Q3 Email Fraud and Identity Deception Trends report that delves into changing techniques used in email fraud and scams, during the April to June 2019 period.
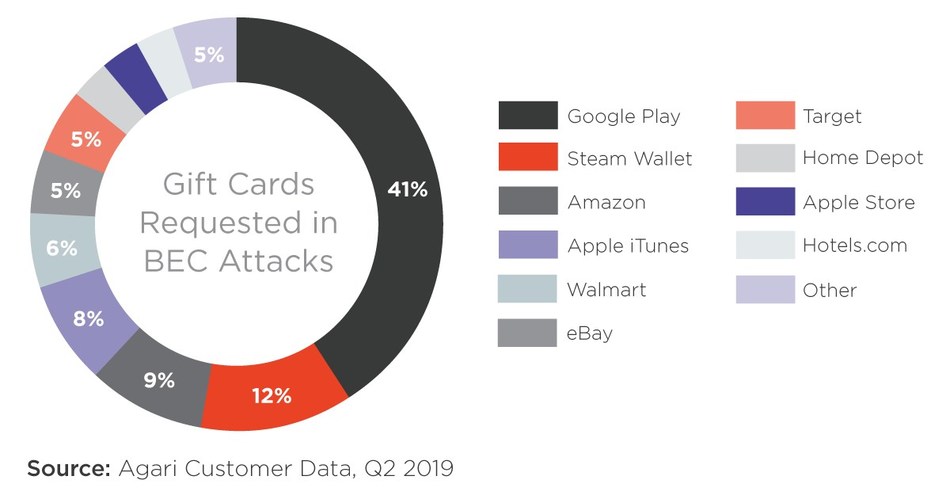
The top finding shows that fraudsters continue to shift away from their traditional methods. Gift cards have become the preferred mode that fraudsters are using to cash out their proceeds. Of the business email compromise attacks that Agari observed during the second quarter, 65 percent of them are focused on gift cards. Specifically, fraudsters tend to request that unwitting victims purchase gift cards and send them to the scammer under various pretenses, such as gifts for customers or rewards for employees.
Marketing Technology News: TIBCO Spotfire X Recognized by SIIA as Best Business Intelligence Reporting & Analytics Solution
Three-quarters of the gift cards requested by fraudsters belong to five brands: Google Play, Steam Wallet, Amazon, Apple iTunes, and Walmart (see accompanying chart).
Gift cards are easy for fraudsters to launder and are hard to trace, which are likely the reasons for their popularity. The downside for fraudsters is that the payout isn’t as large as with wire transfer scams.
Patrick R. Peterson, CEO, Agari, stated: “Business Email Compromise is not only a massive problem but it also continues to perplex organizations. Fraudsters have perfected their social-engineering craft, having now gone low-tech to outsmart high-tech solutions that are meant to detect and stop them. What this study clearly shows is that brand impersonations are in style and gift cards are the new money mule.”
Marketing Technology News: Alibaba.com Opens Platform to Empower US Small Businesses to Sell to the World
Other Email Security Trends
Agari’s Q3 2019 study, which evaluates cybersecurity trends seen from April through June 2019, also found:
- Staffing Gap Becomes Chasm: The need for Security Operations Center (SOC) analysts skyrocketed over a 90-day period by 44 percent, based on an increase in employee-reported phishing and the time required to respond.” The cyber-worker shortage causes a pressure-cooking environment within the SOC at companies, as more incidents are reported and the time to remediate increases. Companies aren’t detecting phishing incidents fast enough, which puts each organization at greater risk of breaches or fraud. Bottomline, SOCs cannot keep up and need to look to automation technology to get ahead.
- 2020 Election Security: 85 percent of today’s major presidential campaigns continue to rely solely on the easily- evaded security controls built into their email platforms—predominantly Microsoft Office 365 and Google Suite. Only 23 percent of candidates have implemented advanced email security and/or email authentication. Despite the relative ease of implementing advanced email protection, ACID finds that only two of the top 13 U.S. presidential candidates with an email-receiving domain or campaign website have implemented a solution to stop advanced threats.
- Game of Clones: 48 percent of attacks are Brand Identity Deceptions. This sudden spike in phishing attacks impersonating trusted brands is rapidly reshaping the email threat landscape. Today, 60 percent of phishing campaigns employing identity deception tactics use display names designed to fool recipients into believing they’re being sent from a known and trusted individual or brand. During the second quarter, however, nearly half (48%) impersonated prominent brands in the initial email—a sharp rise from 34 percent seen in the previous quarter. Just 12 percent of identity-deception attacks impersonated individuals during Q2.
Marketing Technology News: Dods Group Plc Acquires Meritgroup Limited, a B2B Data and Technology Specialist











