AdSecure, the innovative cybersecurity company monitored malicious activity from 1 March to 15 April 2020 to see how the COVID-19 epidemic was being exploited by bad actors. As millions of people are now working from home, where online security isn’t as stringent compared to office cybersecurity systems, the pandemic has created a perfect storm for malvertisers.
“Malicious attacks grew exponentially alongside lockdowns and hit a peak of +116.14% on 28 March”
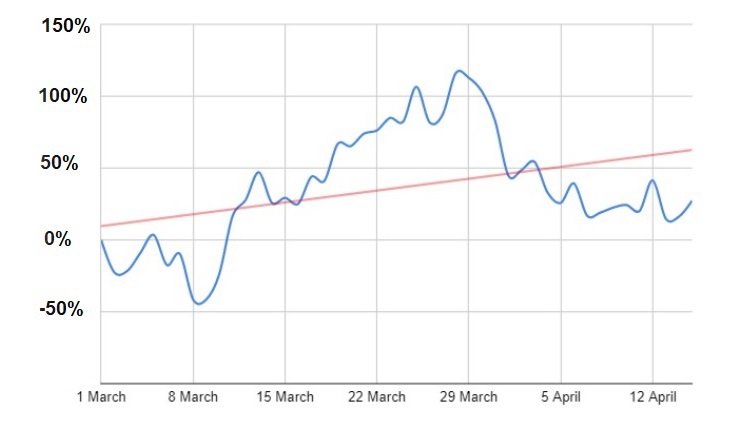 As lockdowns began to be introduced across the globe, the number of attacks increased dramatically, the blue line represents the percentage rate of malvertising attacks based on comparing daily data with the number of attacks on 1 March, and the red line represents the trend analysis.
As lockdowns began to be introduced across the globe, the number of attacks increased dramatically, the blue line represents the percentage rate of malvertising attacks based on comparing daily data with the number of attacks on 1 March, and the red line represents the trend analysis.
We observed an increase in threats worldwide, particularly in the digital advertising ecosystems of prized “Tier 1” GEOs. Though subsiding somewhat from the massive spikes in late March, threat levels remain strong through the first half of April, with a more consistent, sustained pattern of attack, remaining significantly higher than levels detected during the first half of March.
Marketing Technology News: RPA Leaders Kryon and Everest Group Meet Online to Discuss Automation in the New Normal
Malvertiser’s w eapons of choice
 “Malvertisers using well known logos including the World Health Organisation logo to fool users into clicking on malware ads”
“Malvertisers using well known logos including the World Health Organisation logo to fool users into clicking on malware ads”
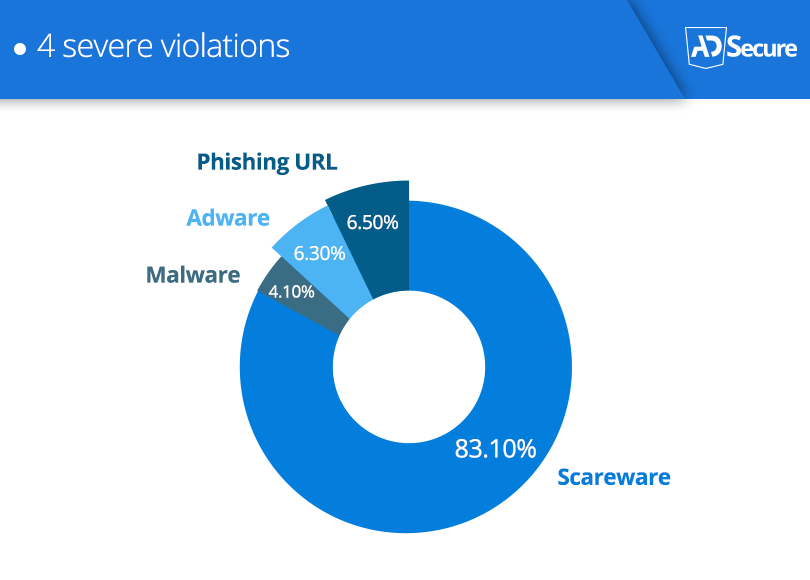
When analysing data on threat levels, we identified specific increases in the deployment of 4 types of malvertising attacks: Adware, Malware, Phishing Scams, and a very heavy use of Scareware attacks. Many of these attacks made use of major branding that would be instantly familiar to their intended targets. Phishing attacks leveraging fake Walmart offers in the US, Intermarche in France, and Amazon in multiple countries.
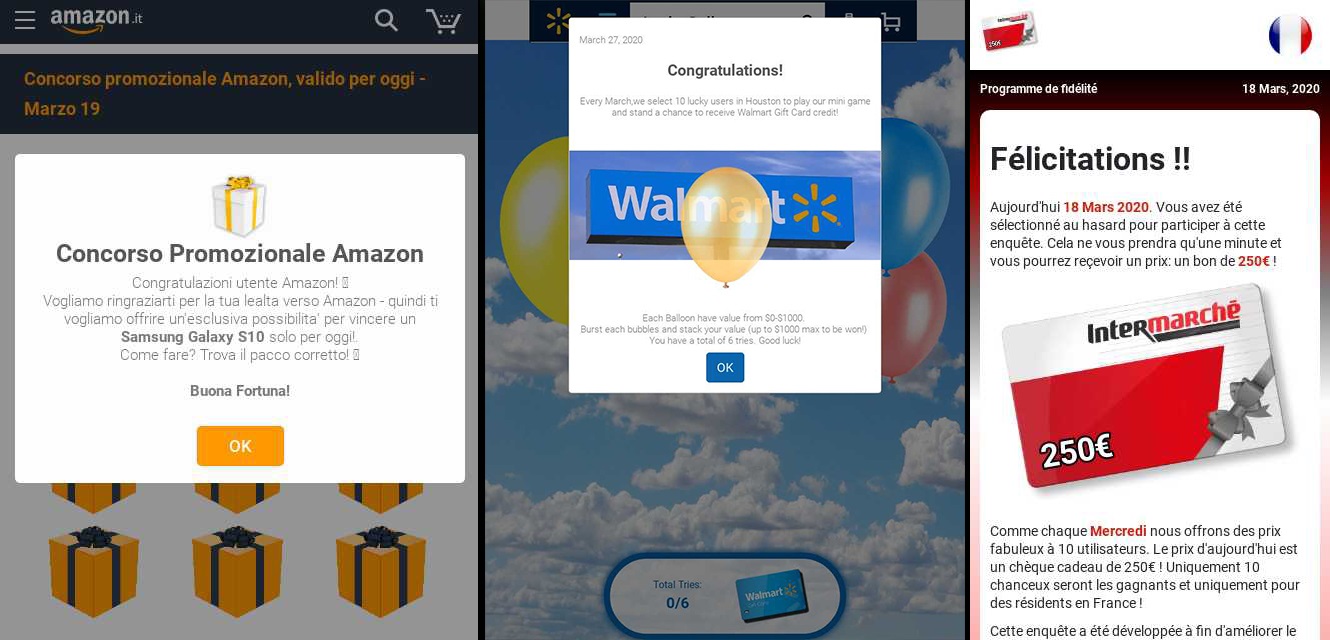 With the terms “Coronavirus”, “COVID-19”, and WHO (Word Health Organisation) in the news constantly malvertisers are using them to manipulate users, playing on their fears and anxieties to get them engaged with bad ads containing Malware. In the example below, AdSecure found a mobile banner ad in Italian, one of the countries worst hit by the pandemic. The ad delivers Malware via an auto-download, using the logo of the World Health Organisation (WHO) and GooglePlay logo to imply legitimacy.
With the terms “Coronavirus”, “COVID-19”, and WHO (Word Health Organisation) in the news constantly malvertisers are using them to manipulate users, playing on their fears and anxieties to get them engaged with bad ads containing Malware. In the example below, AdSecure found a mobile banner ad in Italian, one of the countries worst hit by the pandemic. The ad delivers Malware via an auto-download, using the logo of the World Health Organisation (WHO) and GooglePlay logo to imply legitimacy.
Marketing Technology News: 2Checkout Reports: COVID-19 Impact on Global Online Sales
 The text translates to:
The text translates to:
Ways to get rid of Coronavirus
Download the life saving form here to stop this global pandemic
However the text is not grammatically correct in Italian, so was obviously translated from another language in Google Translate perhaps, so hopefully that deterred some end users from clicking on the banner ad.
“Scareware has been the preferred choice of the cyber criminal”
Above all, the favourite attack delivery method during this spike in malicious activity appears to be Scareware, fake alerts claiming an imminent or existing threat to a user’s device, which of course does not exist and is designed to trick the user for falling into a scam. Scareware attacks grew exponentially, if we take the data from 1 March as the control, by 4 March there was a 485% increase, 6 March a 2,628% increase and by 8 March a 3,342% increase where it remained at this new high right through to 15 April.
While the style and tone of Scareware attacks can vary, we often see these take the form of a tech support scam, wherein users are alerted that their system is infected with certain types of virus, or spyware. Again, cyber criminals often rely on the iconography of well known brands to imply legitimacy, convince users that they will indeed be contacting Microsoft technical support, as seen in the examples below:
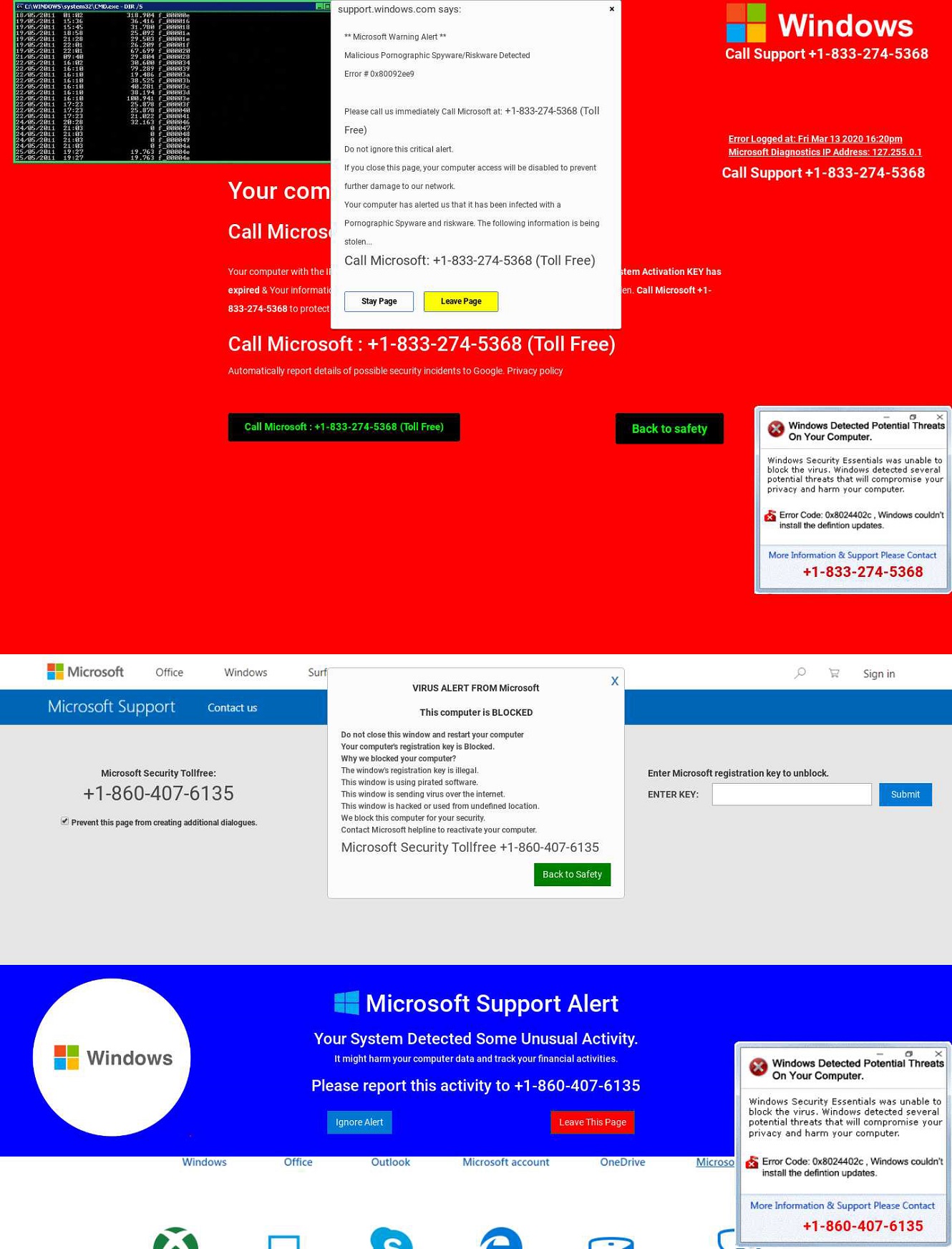 Of course, the user isn’t contacting Microsoft, they’re falling into a trap.
Of course, the user isn’t contacting Microsoft, they’re falling into a trap.
“Bad ads surged globally, but the US got hit particularly hard”
AdSecure examined which were the top 5 GEOs that received the highest malvertising attacks:
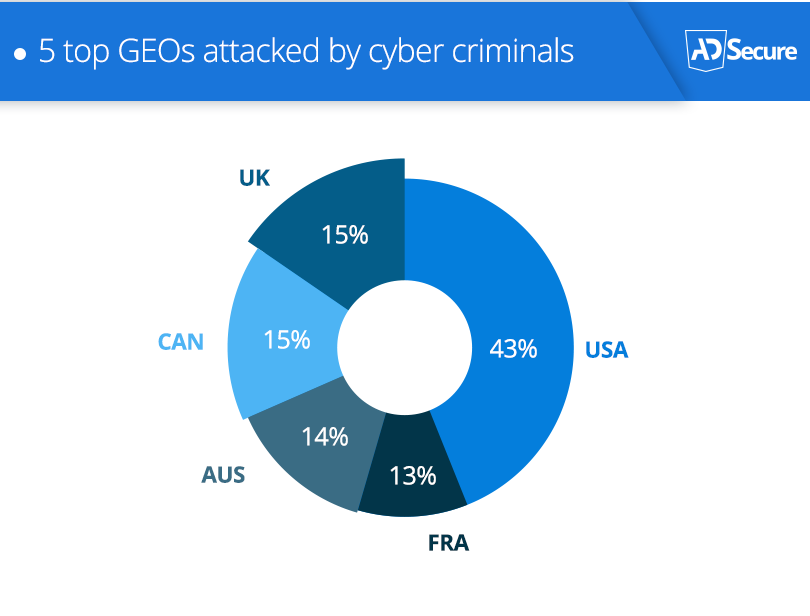 Tier 1 GEOs faced a wave of attacks with malvertisers heavily targeting the United States with detected threats in the US nearly 3x higher than in the other top 4 GEOs.
Tier 1 GEOs faced a wave of attacks with malvertisers heavily targeting the United States with detected threats in the US nearly 3x higher than in the other top 4 GEOs.
“Windows PCs and iPhones were among malvertisers’ top 5 device choices”
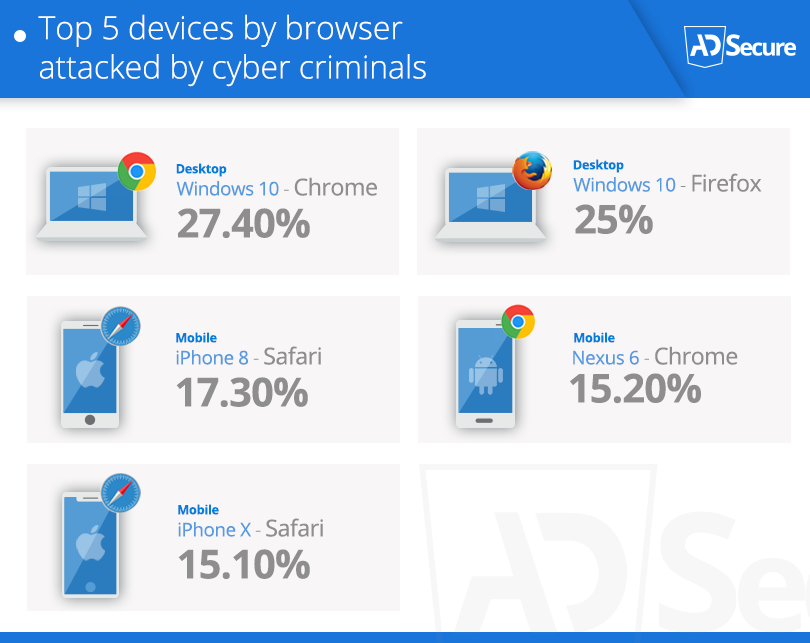 Windows laptops and PCs came out on top as malvertisers attacked users working from home. For Apple users the iPhone 8 and iPhoneX were top of the cybercriminal devices to attack.
Windows laptops and PCs came out on top as malvertisers attacked users working from home. For Apple users the iPhone 8 and iPhoneX were top of the cybercriminal devices to attack.
AdSecure’s sales manager Bryan Taylor commented, “There isn’t much safety to be found in any particular device and browser combination, either, as throughout March and April we can see that threats are being detected consistently across multiple devices and browsers. With more people frequently browsing on both their desktop and mobile devices and using multiple browser options, malvertisers can spread their attacks accordingly, maximising the effective impact of each bad ad campaign they are running.”
Marketing Technology News: Tata Consultancy Services Teams With Creatio to Support Organizations Fighting Against COVID-19
Taylor continued, “With this sustained increase in malicious activity within the digital advertising ecosystem, it’s likely that as social distancing measures, and lockdowns continue while the world get’s a collective handle on the Covid-19 crisis, cyber criminals will continue to take advantage of the situation by deploying malicious ads, and it is vital that the industry remain vigilant in the fight against malvertising, particularly during the unprecedented times we all find ourselves in.”
AdSecure is here to help publishers and ad platforms with the challenge of fighting malicious and poor quality ads while maintaining user safety and experience. Our free trial account is available to anyone looking to #StopBadAds.
Marketing Technology News: Citi Launches Thought Leadership Website for Institutional Investors











