Hidden Mobile Redirects Resulting In Click Fraud Are Estimated To Cost the Industry $920 Million, According to GeoEdge
Auto-redirects are a growing pestilence for publishers: a vehicle for malvertising that seizes users and reroutes them, or a protocol that remains hidden and enables click fraud. Auto-redirects alone cost the industry an estimated $210 million annually, and they also cost it another $920 million by facilitating ads with click fraud. The auto-redirect problem particularly festers in the mobile space and until recently, attacks managed to elude detection by publishers and security experts alike.
GeoEdge ran an in-depth research and discovered distinct classes of redirect attacks and their underlying mechanisms, making it possible to thwart many of the auto-redirects’ countermeasures. Here are the findings of the report;
Threat is Larger For Mobile
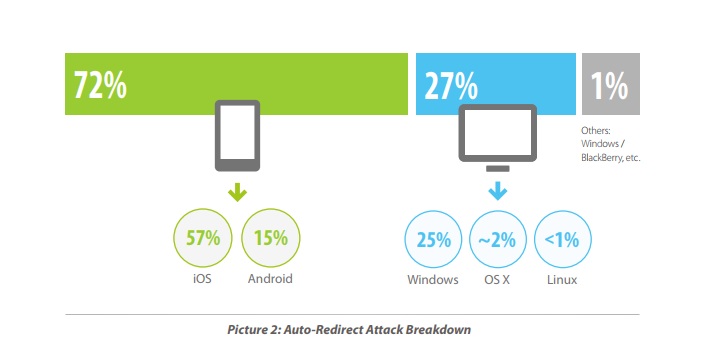
The combination of fear and confusion sown by redirects is particularly pronounced on mobile platforms, and it’s why the technique has such an affinity for phones. While a non-trivial 27 percent of auto-redirects occur on desktops, 72 percent occur on mobile devices, with 57 percent on iOS and 15 on Android.
 For malvertisers, the advantages of auto-redirects generally, and mobile redirects especially, are legion. Ads can redirect to pages, fashioned after Google or Apple, that falsely alert users that their devices are infected or that a free iPhone awaits, in turn pushing them to download malware or dial a scam number. In other words, the schemes are the same as those used for non-redirecting attacks. But by taking users to an entirely separate window – rather than simply an irksome banner ad – the scam can appear more legitimate than it otherwise would. For example, a webpage wholly constructed to look like Microsoft’s site can feel more real than a simple banner ad.
For malvertisers, the advantages of auto-redirects generally, and mobile redirects especially, are legion. Ads can redirect to pages, fashioned after Google or Apple, that falsely alert users that their devices are infected or that a free iPhone awaits, in turn pushing them to download malware or dial a scam number. In other words, the schemes are the same as those used for non-redirecting attacks. But by taking users to an entirely separate window – rather than simply an irksome banner ad – the scam can appear more legitimate than it otherwise would. For example, a webpage wholly constructed to look like Microsoft’s site can feel more real than a simple banner ad.
Attacking banks is hard, while replicating a bank’s web page and getting users to hand over their info is comparatively easy. And to mobile users, a “System Warning!” in the style of a popup notification they regularly see on their phones can seem too real to ignore.
This makes mobile redirects particularly effective for click fraud and for phishing and mining personal data. While scammers can lure users to call a fake number, the distance between a scammy webpage and dialing numbers on the phone involves several steps, each one reducing the chance that the target will fall prey to the trap.
Injecting Malicious Code
Hackers can inject malicious code into the ad creative itself, at the ad request level, or by post-click. These perfectly innocent ads get infected, unbeknownst to anyone in the advertising chain, and a benign ad hosted by a perfectly responsible network now takes the user directly to a tech support scam.
From the perspective of the operating systems’ creators, the problem is difficult to solve. Apple seemed to have addressed auto-redirects to the App Store with iOS 8, but the problem reared its head shortly after, with the release of iOS 10.3. Rinse and repeat. And regrettably for those on Android, mobile redirects have long been a reliable mainstay of their mobile experience.
That’s because it’s difficult for the app store operators to determine whether it was a human or a script that opened the app store to begin with. The mechanism allowing app stores to automatically open without actually clicking the store’s icon is part of what makes the mobile experience seamless.
That mechanism is called a deep link, and it’s why clicking a link to a Twitter handle on a web page will open the Twitter app instead of twitter.com. When it works as intended, it’s convenient. But the same mechanism can be embedded into a web frame by dubious networks.
Locating a Redirect Script
Many redirects execute dynamic, targeted attacks, sending the user to another domain only if certain conditions are met. Examples of such conditions are whether the website is being visited on a mobile device or from a specific country. Redirect attacks can track who has already been redirected to the malicious site or the app store. Scripts often redirect users once and no more; after that, as far as that user is concerned, the malicious script vanishes.
The redirect stops redirecting, thwarting efforts to replicate the problem. Users complain to publishers about being bounced from their site, publishers can’t seem to recreate the problem the users complained about, and redirects live another day.
Identifying and locating a redirect script that is here today and gone tomorrow is just as challenging using typical security measures, which rely on recreating malvertising in mobile emulators. This adaptability is what often makes redirects so peculiarly vexing. Unlike many other forms of attack, redirects can be maddeningly chameleonic, never holding on to a steady form and shifting the moment they seem to have been identified.
Impact on Revenue
$920M Damages from Mobile Click Fraud
GeoEdge determined that click fraud is a part of the underlying mechanism of the attacks discovered. The trouble with hidden redirects is that they are even harder to identify, as they do not obviously affect the user experience. This causes a drain on the publishers’ resources. In a general sense, hidden mobile redirects resulting in click fraud are estimated to cost the industry $920 million.
 $210M Loss for Publishers
$210M Loss for Publishers
With hundreds of millions of impressions impacted by auto-redirect attacks, publishers’ revenues are significantly affected. For publishers who are unable to identify those auto-redirect attacks, the impact is even greater. Hackers continue to target their sites and users. The GeoEdge team estimates that auto-redirect activities cost $210 million annually, including identification, documentation, and remediation.
Read More: eZanga Leverages IBM Cloud to Combat Ad Fraud and Bot Traffic
STATISTICS
- Tactics for Malvertising Distribution Auto-redirects make up 48% of all malvertising events, with malicious URL pre-click far behind at 18%.
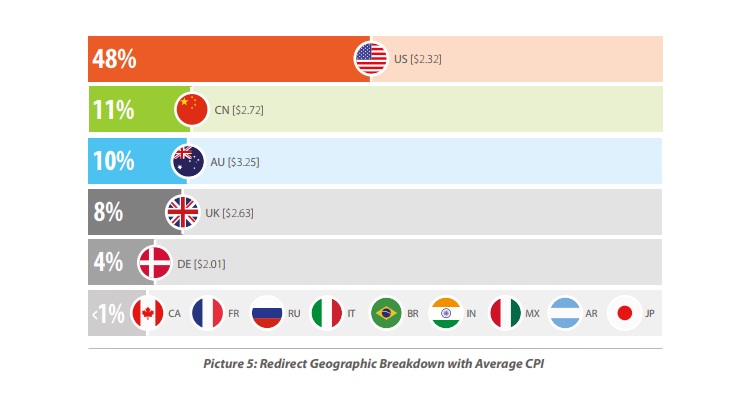
- The US accounts for 48% of auto-redirects, nearly five times as many Canada (the second most targeted) and Australia (the third most targeted).
- A total of 27% occur on desktops and 72% on mobile devices, with 57% on iOS and 15% on Android.
Networks and CPI Incentives
It’s within the app economy that the connections between malvertisers, ad networks and app developers become a kind of toxic mix. App designers give their ads to ad networks that are charged with the sole task of increasing downloads. Unfortunately, different networks, behave with different degrees of integrity, and app makers are dismayingly likely to look the other way at whatever underhanded tactics the networks employ to make downloads happen. And because networks are paid on the basis of cost-per install, or CPI, incentives between networks and users can become wildly misaligned.
CPIs don’t come cheap – globally, as of last year, the average CPI was $1.24 for iPhone apps and $0.53 for those on Android. That’s probably why redirects, whether to app stores or to phishing scams, occur on iOS nearly four times as often as they do on Android: By nearly every metric – including personal income, money spent on apps and time spent on their phones – iOS users are more valuable. That makes them equally valuable to malvertisers.
So the networks follow a simple, shortsighted math: swamp users with redirects to the app, expect that most of them will be so furious at having been shooed out of their webpage that they’ll forever consider the app a nuisance, and at the same time plan for a tiny fraction which, out of confusion or a spontaneous impulse to download the app, will actually install it. The number of installs could be far below even single-digit percentages, but given sufficient volume, that’s enough. The more users who are annoyed, the more money is made.
A CPI in the United States costs on average $2.32, slightly less than an install in Australia at $3.25 or one in Canada at $2.72.
GeoEdge is the premier provider of ad verification and transparency solutions for the online and mobile advertising ecosystem.
Recommended Read: A4G Taps Anura for Their Real-Time Ad Fraud Detection











